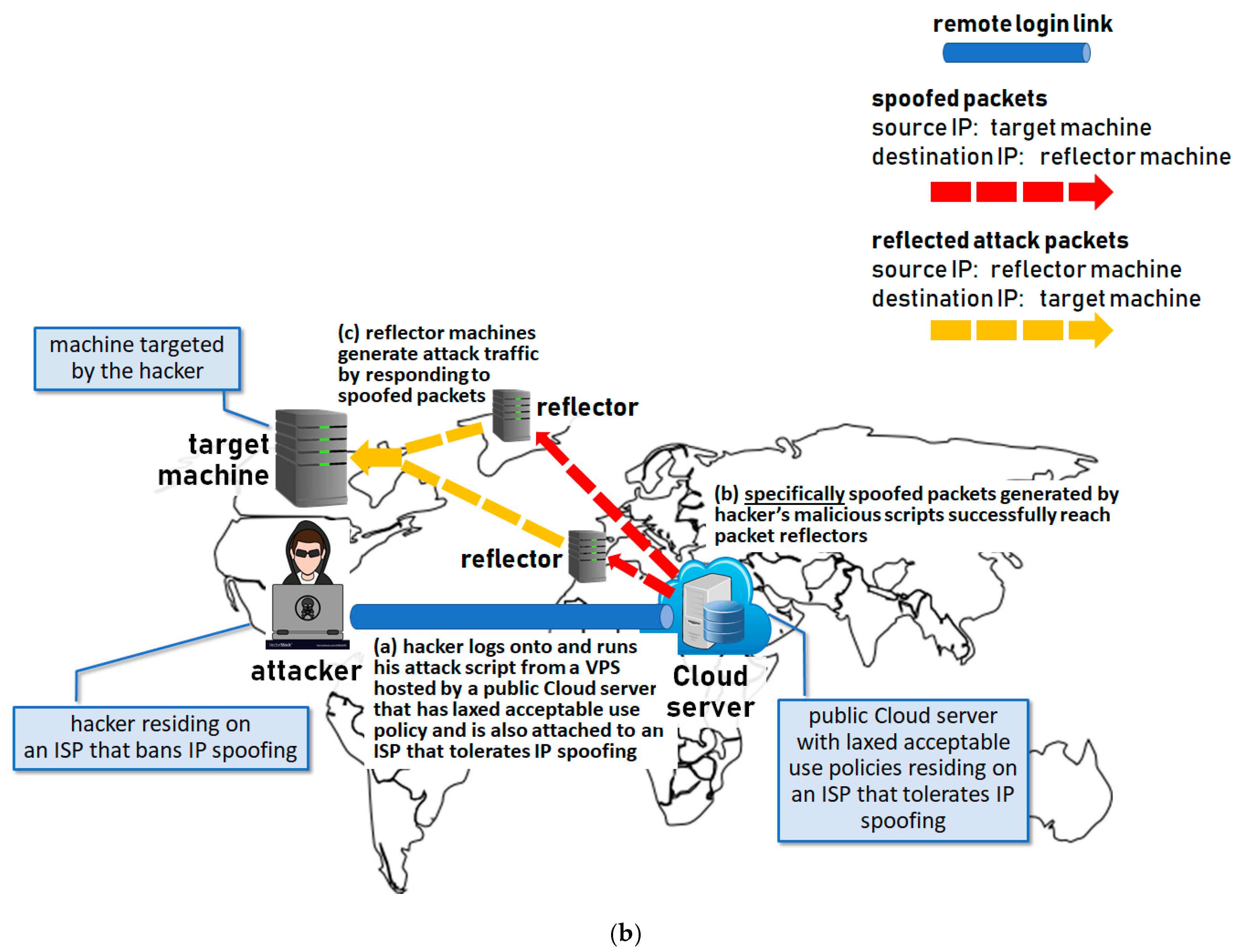
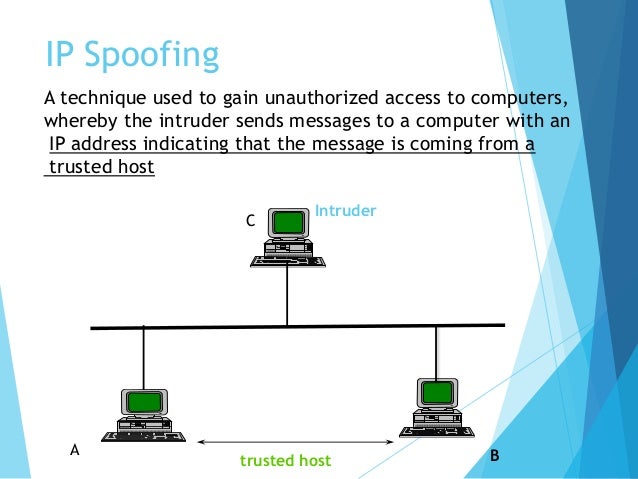
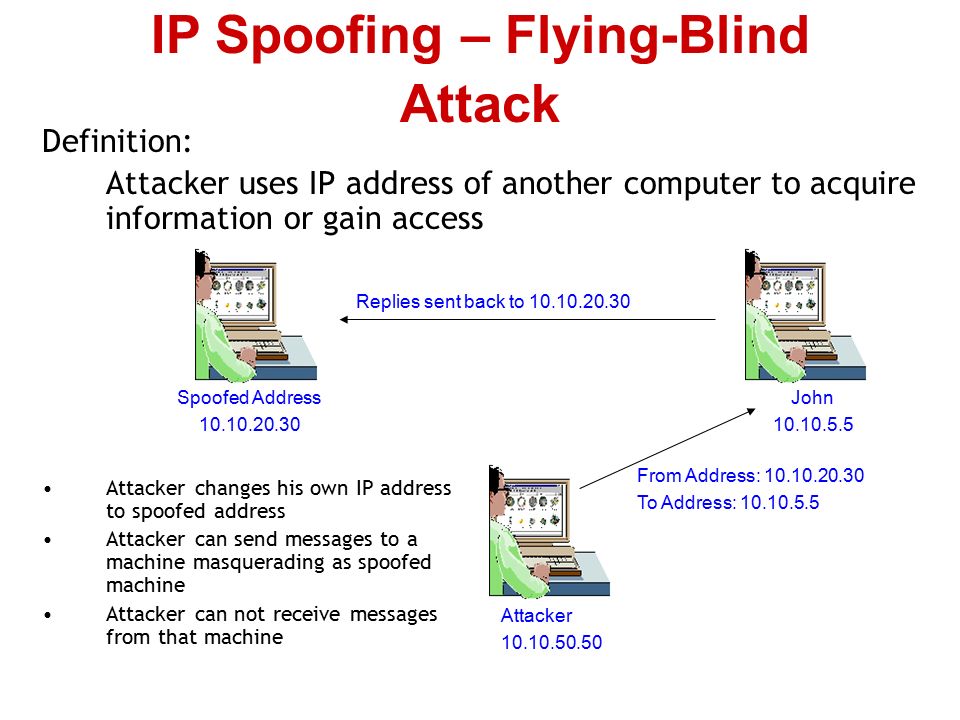
Definition For Ip Spoofing

Deze activiteiten houden in dat specifieke eigenschappen van het e mailbericht zoals from van return path afzender en reply to antwoorden naar worden gewijzigd.
Definition for ip spoofing. E mail spoofing is een term die gebruikt wordt om frauduleuze e mailactiviteiten te beschrijven. The access control device saw the ip address as it is trusted and then lets it through. Deze truc is alleen in zeer uitzonderlijke situaties toe te passen en komt daardoor weinig voor. Ip spoofing is the action of masking a computer ip address so that it looks like it is authentic.
Wil je meer weten over spoofing. Een andere vorm van spoofing is ip adresspoofing. Bij deze truc nemen criminelen een ip adres van anderen over. During this masking process the fake ip address sends what appears to be a malevolent message coupled with an ip address that appears to be authentic and trusted.
Hierdoor lijkt het alsof de e mail afkomstig is van een andere bron. Attacker puts an internal or trusted ip address as its source. Ip spoofing is the creation of internet protocol ip packets which have a modified source address in order to either hide the identity of the sender to impersonate another computer system or both. In computer networking ip address spoofing or ip spoofing is the creation of internet protocol ip packets with a false source ip address for the purpose of impersonating another computing system.
Internet protocol spoofing of ip spoofing is een techniek om ongeautoriseerde toegang te verkrijgen tot een computer via diens ip stack. What is ip spoofing. What is ip spoofing. It is a technique often used by bad actors to invoke ddos attacks against a target device or the surrounding infrastructure.
Ip spoofing as the name suggests ip spoofing refers to the use of a fake ip address by the sender to either disguise their real identity or to carry out cyber attacks. Ip spoofing is a technique used to gain unauthorized access to computers where by the attacker send messages to a computer with a foreign ip address indicating that the message is coming from a trusted host. The sender assumes an existing ip address that doesn t belong to them in order to send out ip packets to networks they otherwise wouldn t have access to.