Definition Of Hashing Algorithm

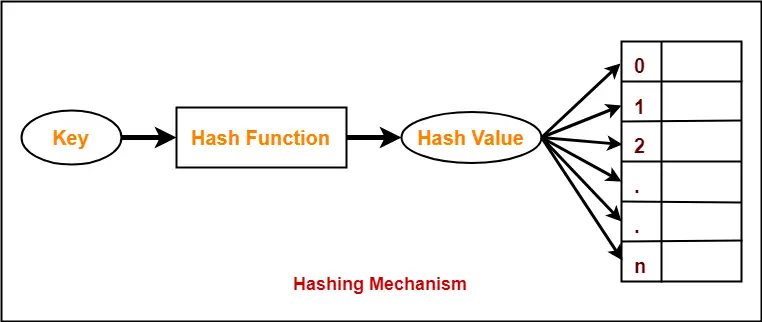
Searching for the item follows the same procedure until the item is located an open slot is found or the.
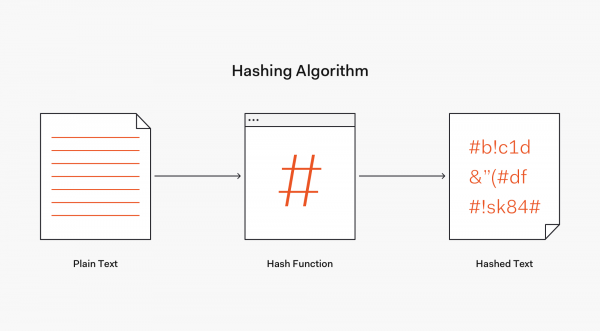
Definition of hashing algorithm. Compare the features and functionality of five prominent patch management tools for microsoft and third party applications to. It is a mathematical algorithm that maps data of arbitrary size to a hash of a fixed size. As every file on a computer is ultimately. The output string is generally much smaller than the original data.
In open address hashing the table is probed starting from the occupied slot in a specified manner usually by linear probing quadratic probing or double hashing until an open slot is located or the entire table is probed overflow. This is a very simple example but it gives us an idea about what a hashing algorithm can look like. A good hashing algorithm would exhibit a property called the avalanche effect where the resulting hash output would change significantly or entirely even when a single bit or byte of data within a file is changed. 5 wsus alternatives for patch management.
A hash function that does not do this is considered to have poor randomization which would be easy to break by hackers. To learn more about hashes check this very thorough wikipedia page. A hashing algorithm is a cryptographic hash function. What does hashing algorithm actually mean.
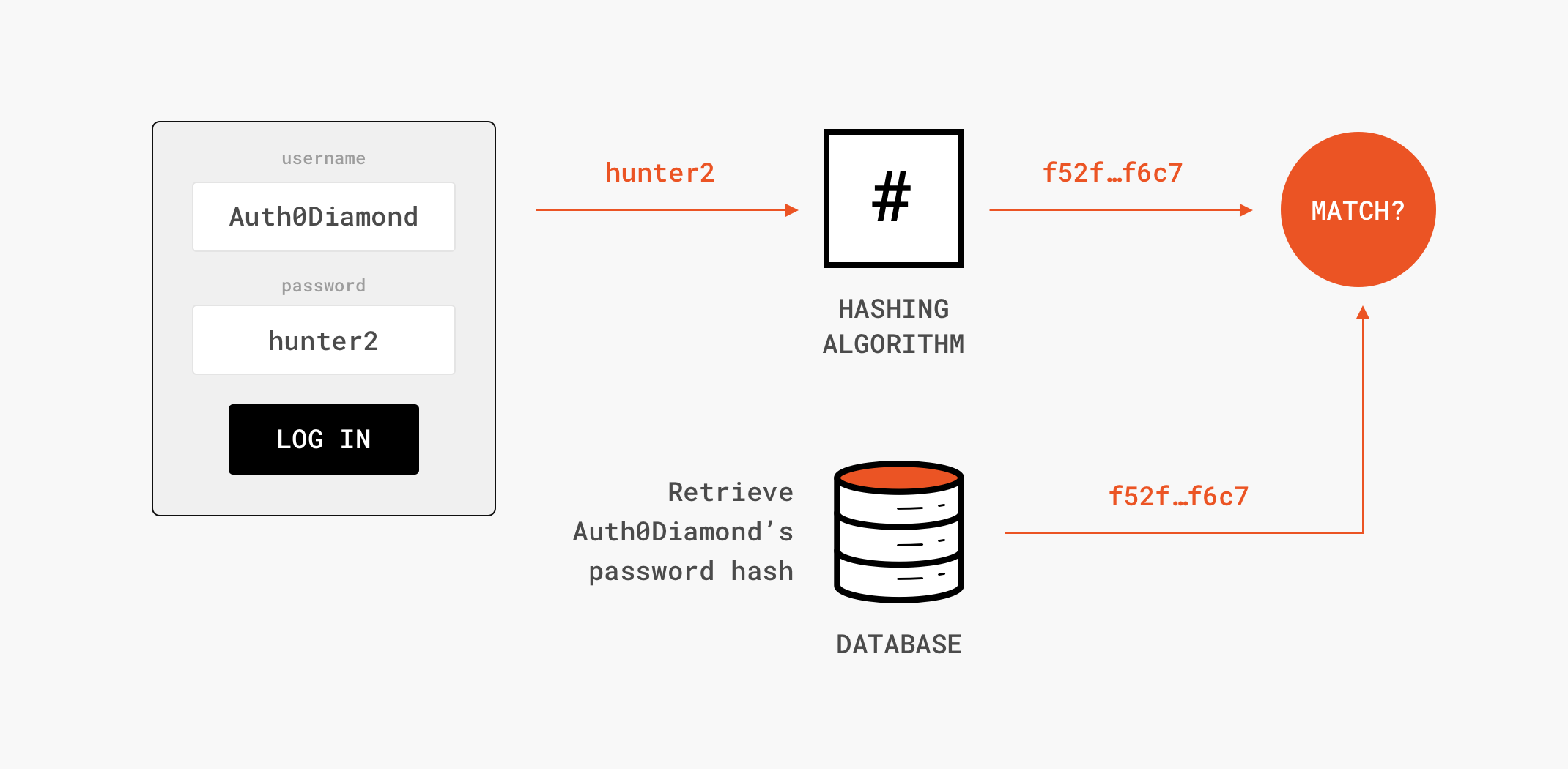
This definition is for personal use only. Find out inside pcmag s comprehensive tech and computer related encyclopedia. Then there s also the use of hashing in database retrieval. These are called hybrid encryption systems.
Hashes are the output of a hashing algorithm like md5 message digest 5 or sha secure hash algorithm. These algorithms essentially aim to produce a unique fixed length string the hash value or message digest for any given piece of data or message. Using hashing in database retrieval. A hash algorithm is a function that converts a data string into a numeric string output of fixed length.
What is a hashing algorithm. Derrick rountree in security for microsoft windows system administrators 2011.