Definition Of Rsa Algorithm

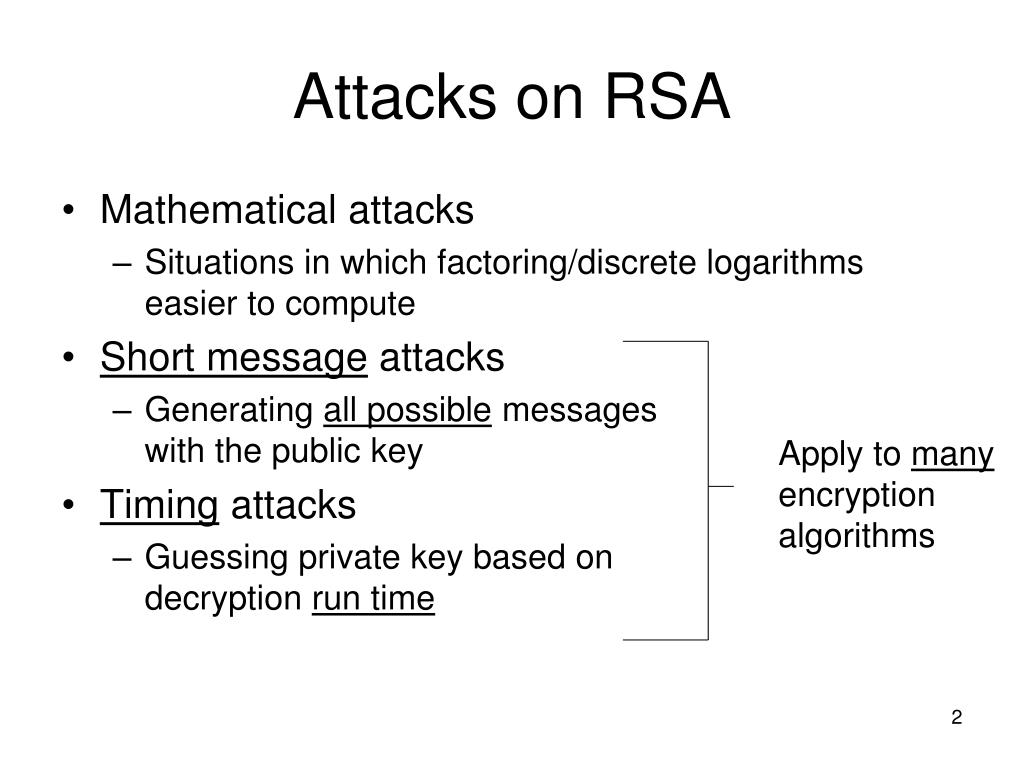
Deducing an rsa key therefore takes a huge amount of time and processing power.
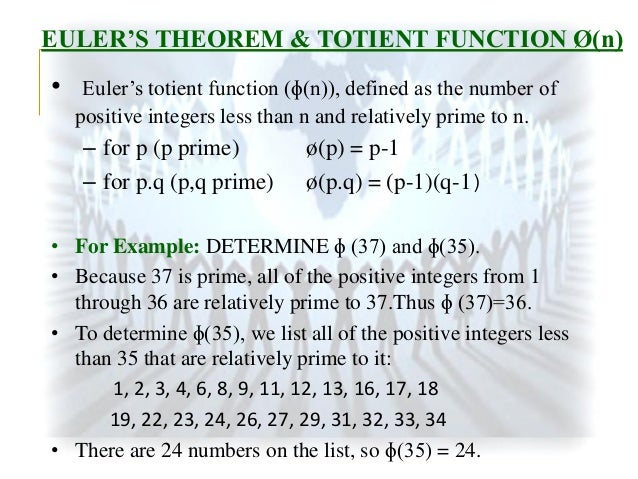
Definition of rsa algorithm. A public key encryption technology developed by rsa data security inc. Asymmetric actually means that it works on two different keys i e. American heritage dictionary of. As the name describes that the public key is given to everyone and private key is kept private.
The algorithm capitalizes on the fact that there is no efficient way to factor very large 100 200 digit numbers. It was invented by rivest shamir and adleman in year 1978 and hence name rsa algorithm. Public key and private key. She won several prizes including an intel award for excellence in science.
It uses both private and public key keys should be very large prime numbers. Rsa algorithm is a public key encryption technique and is considered as the most secure way of encryption. The rsa algorithm is based on the difficulty in factoring very large numbers. Rsa algorithm synonyms rsa algorithm pronunciation rsa algorithm translation english dictionary definition of rsa algorithm.
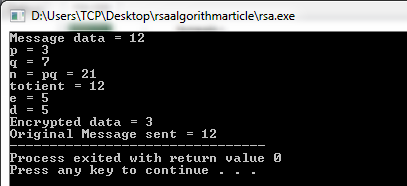
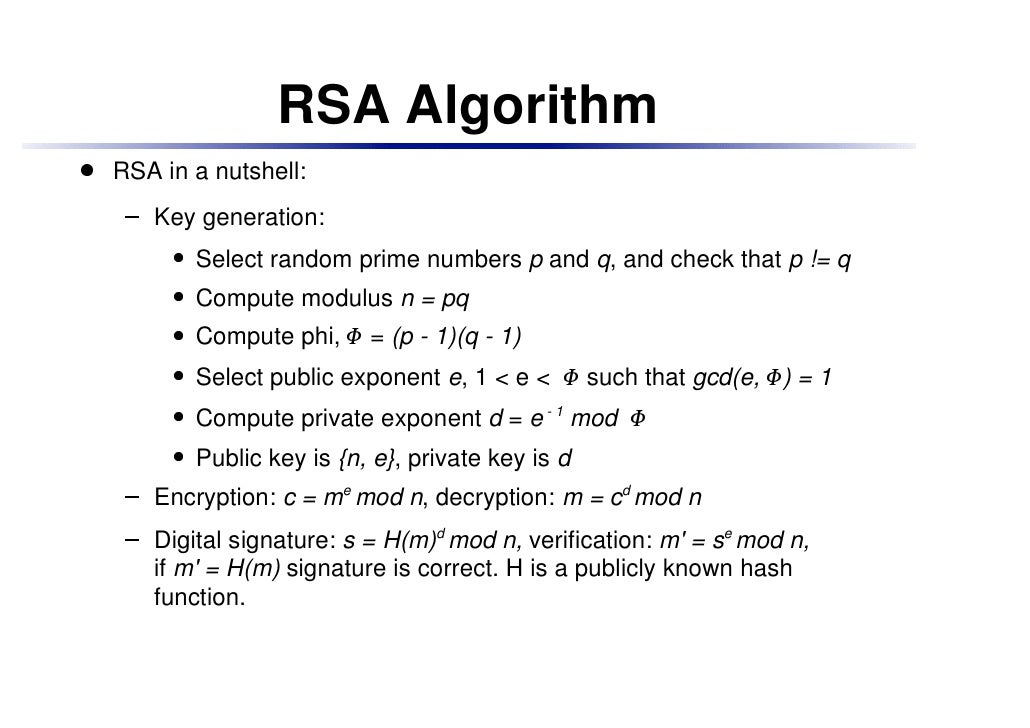
Using an encryption key e n the algorithm is as follows. Rsa is a cryptosystem for public key encryption and is widely used for securing sensitive data particularly when being sent over an insecure network such. The rsa algorithm the rivest shamir adleman rsa algorithm is one of the most popular and secure public key encryption methods. Rsa algorithm is asymmetric cryptography algorithm.
The acronym stands for rivest shamir and adelman the inventors of the technique. Based on this principle the rsa encryption algorithm uses prime factorization as the trap door for encryption. An algorithm used in public key cryptography commonly used in various protocols for secure online transmission of data. An example of asymmetric cryptography.
The rsa algorithm is based on the fact that there is no efficient way to factor very large numbers. The rsa algorithm and the company that markets it were named for ronald rivest adi shamir and leonard adelman who published it in 1977 this project suggested by her father required sarah to learn a computer programming language and to study mathematics as well as cryptography the effort paid off.